Curtain LogTrace
The Comprehensive File Activity Monitoring and Auditing Tool

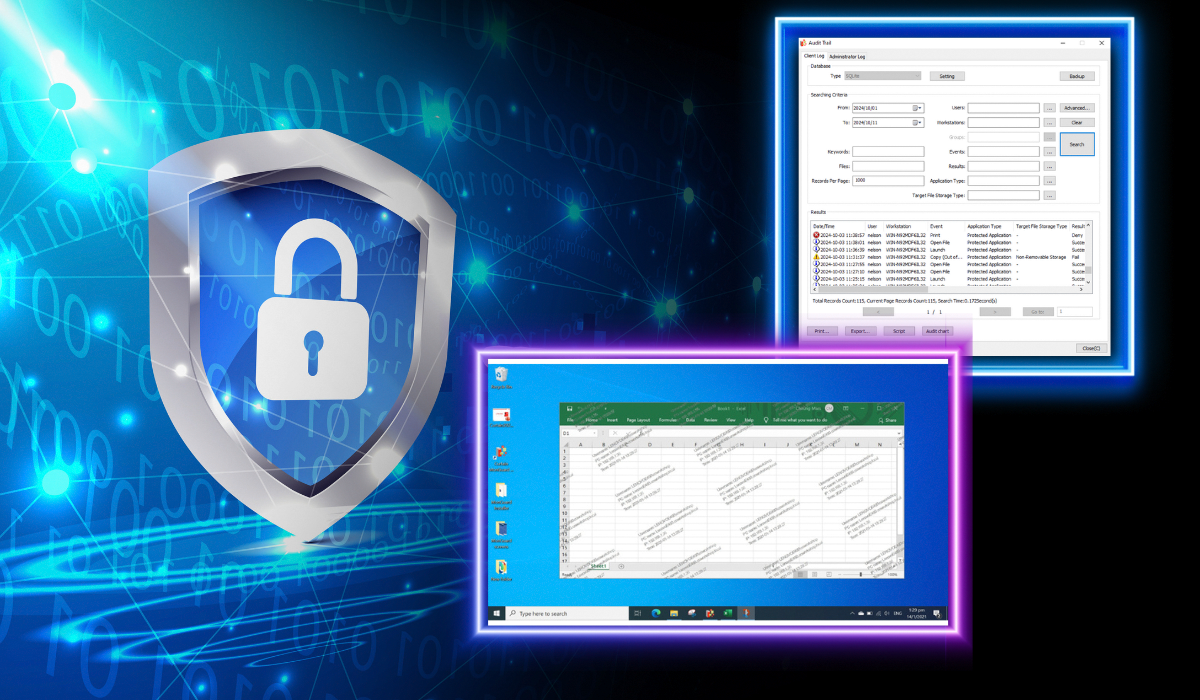
Curtain LogTrace is a comprehensive file activity monitoring and auditing solution that enhances security and accountability across your organization. By providing detailed insights into file-related actions, including access, modifications, and deletions, Curtain LogTrace enables organizations to maintain clear audit trails and meet compliance requirements. Ideal for compliance audits, activity reviews, and operational transparency, Curtain LogTrace empowers businesses to monitor user file activities across their digital assets and ensure accountability in file interactions.
Top Features of Curtain LogTrace

Comprehensive File Activity Logging
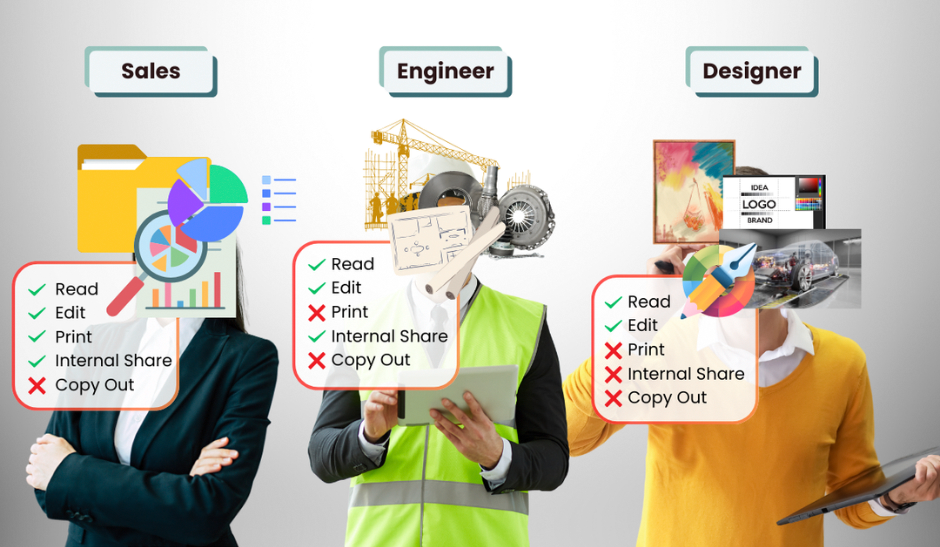
Track detailed actions on files, including creation, deletion, copying, moving, printing, and renaming*, ensuring full visibility of file operations.
*Renaming and printing are only available for the paid version
Application Activity Tracking*

Monitor file activities within applications, capturing events like saving, opening, and closing files for enhanced oversight of user interactions.
*For paid version only.
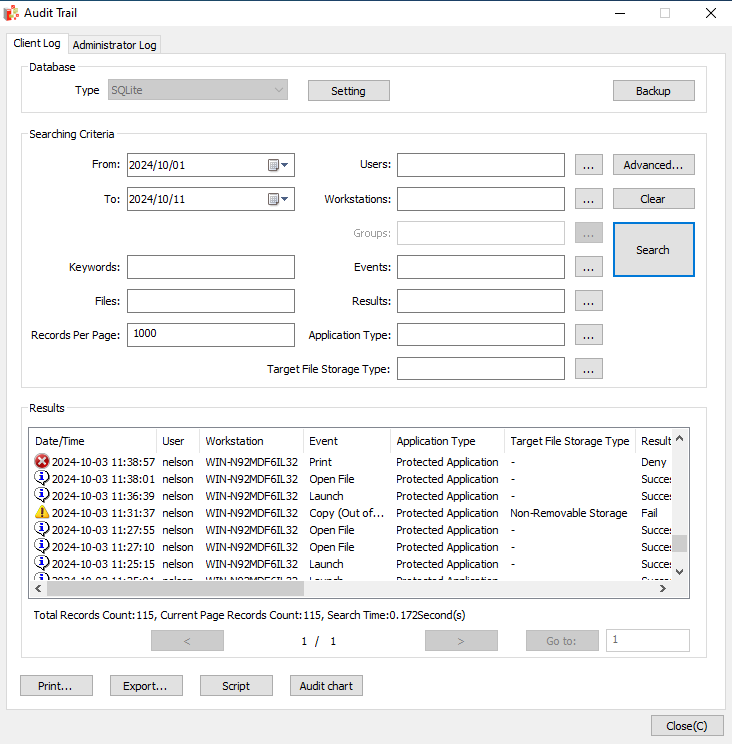
Database Support and Maintain Integrity*

Curtain LogTrace seamlessly integrates with popular databases, including MySQL and Microsoft SQL, for robust and scalable data management. It is designed with security at its core, ensuring that all log data remains trustworthy and protected. It employs secure storage mechanisms and access controls to prevent tampering, guaranteeing that audit records are complete and unaltered.
*For paid version only.

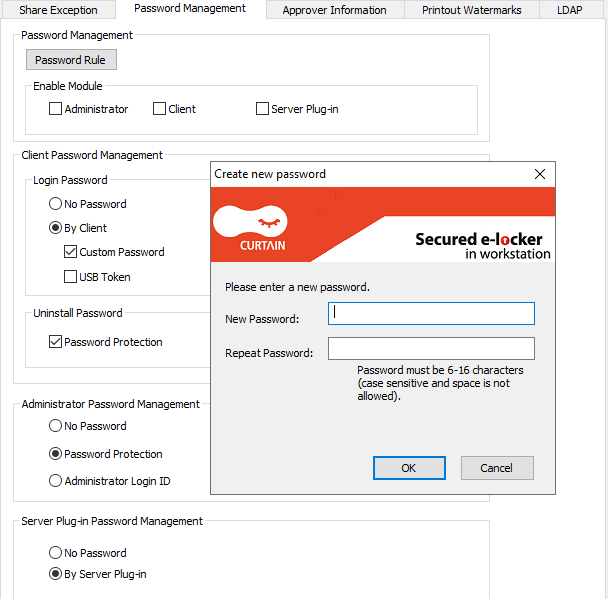
Client Uninstall Protection*

Enforce secure software removal with a required uninstall password, preventing unauthorized uninstallation by end users.
This feature is handy for organizations that want to prevent unauthorized removal of critical software. Adding this password requirement significantly reduces the risk of accidental or malicious uninstallation.
*For paid version only.
Logging for Removable Storage Activities

Curtain LogTrace extends its auditing capabilities to external storage devices such as USB drives and external hard disks. It identifies and records the connection of these external devices. By capturing detailed records of file transfers to and from these sources, it helps organizations monitor potential data exfiltration points and maintain a clear record of how sensitive information is handled outside the core infrastructure. This added visibility strengthens data protection strategies and supports compliance with policies governing removable storage use.

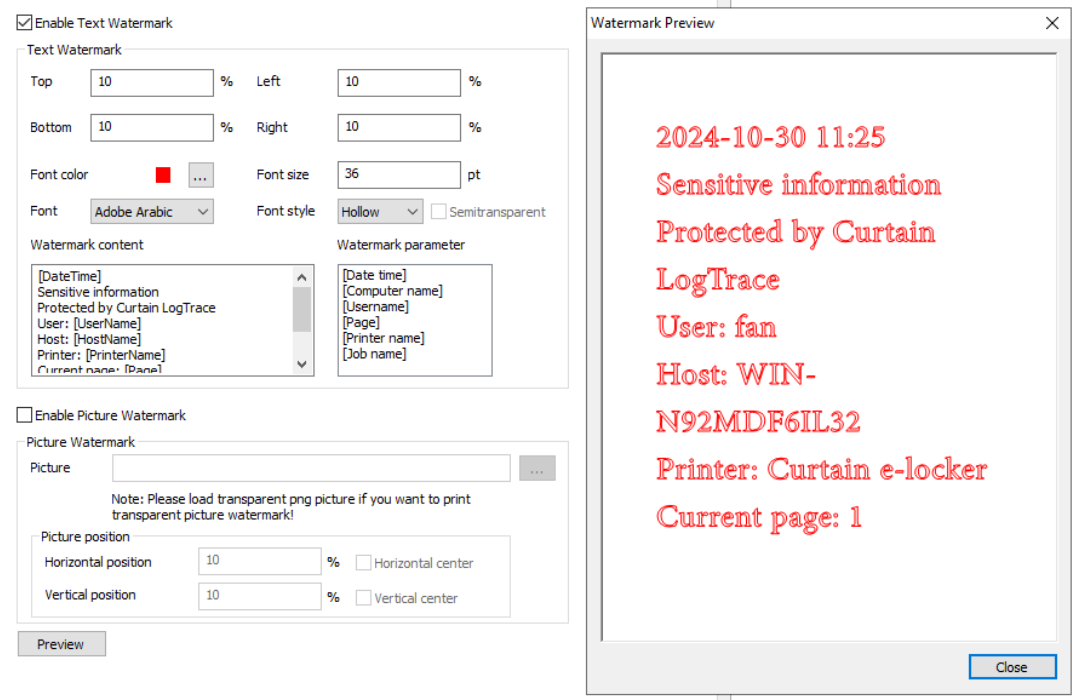
Print Watermark*

Add watermarks to printed documents, providing an additional layer of security to sensitive information when printed.
*For paid version only.
Centralized Administration

Manage all configurations, policies, and logs from a central management console, simplifying administration across large environments.
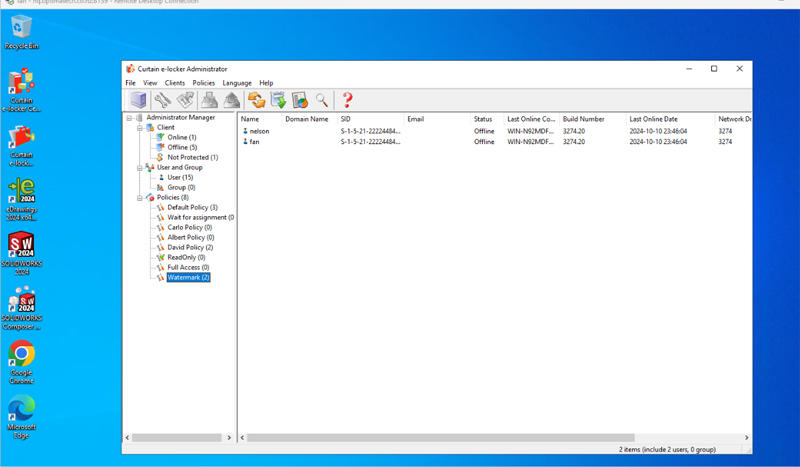
Active Directory Integration

Leverage existing Active Directory infrastructure to streamline deployment and configuration.

Upcoming Features of Curtain LogTrace
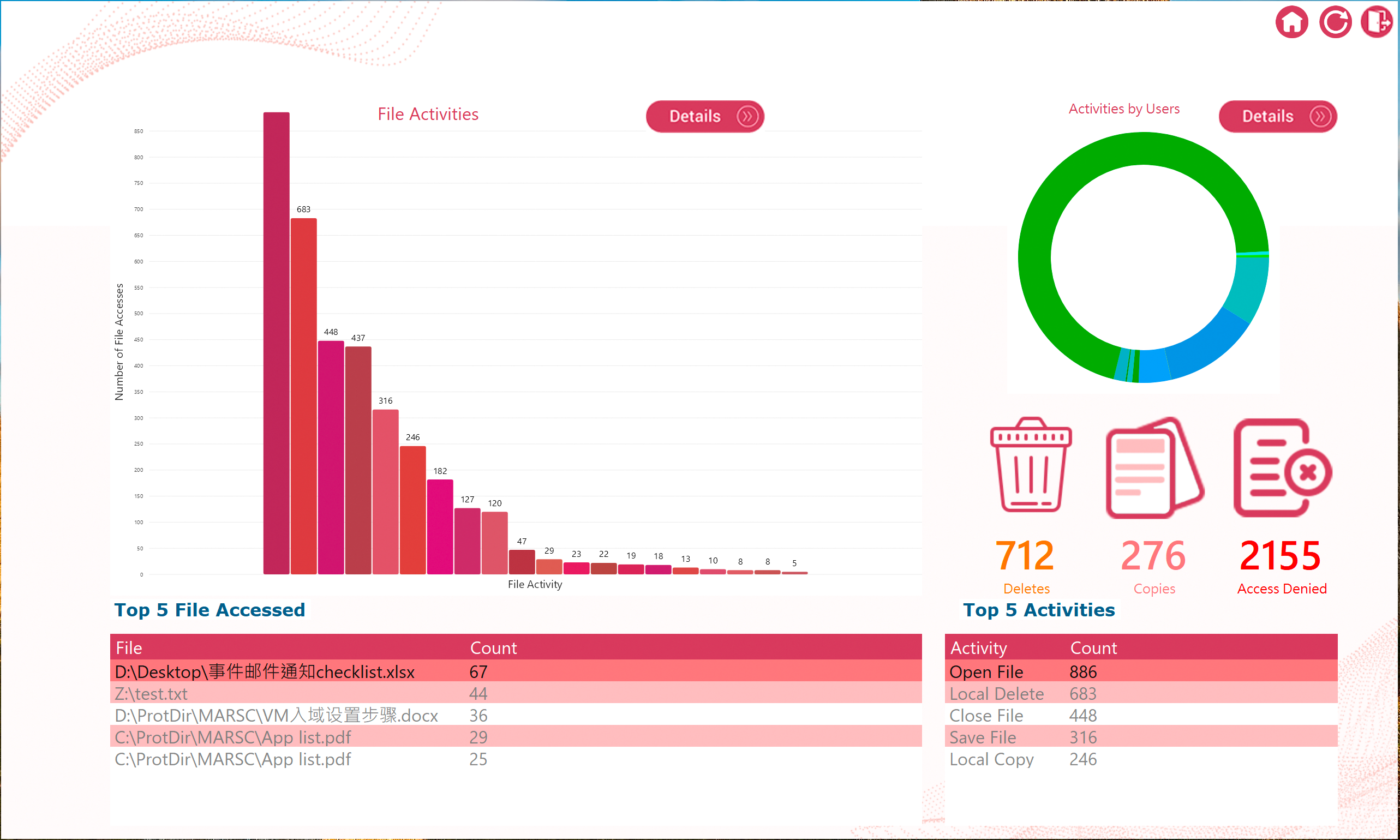
Curtain Report*
Introducing Curtain Report, an advanced analytics and reporting module designed to transform Curtain LogTrace file activity logs into actionable insights. This feature will provide businesses with meaningful statistics that highlight the top 5 most accessed files, identify the most active users, and track the count of file access like delete/ rename/ move/ denials etc. Powerful, advanced log searching capabilities will enable quick filtering and pinpointing of specific events, streamlining investigations and audits. Curtain Report will empower teams to gain deeper visibility, improve decision-making, and enhance overall operational oversight.
*This feature will be on upcoming paid version only.
Cloud Storage Services Auditing*
Soon, Curtain Report will expand its auditing capabilities to include cloud storage services like OneDrive, Google Drive, Dropbox, and others. This feature will enable organizations to track file activities—such as uploads, downloads, edits, and deletions—that occur within designated Cloud Storage Services. By consolidating file activity logs of both locals and cloud storage services, this enhancement will offer greater transparency into data movement, helping to mitigate risks associated with shadow IT, data leakage, and compliance gaps.
*This feature will be on upcoming paid version only.

Customised Monitoring Paths and Alert Setting*
Additionally, administrators will be able to specify critical paths—such as Finance, HR, or new Projects—for focused monitoring. Custom alert criteria can be configured to flag activities like bulk downloads, access outside of business hours, or deletion of sensitive documents. When such events occur, Curtain Report will automatically generate alerts and send detailed notifications to designated recipients, such as security teams, compliance officers, or department heads, ensuring timely awareness and response.
*This feature will be on upcoming paid version only.

Curtain LogTrace Introduction
Benefits

Enhanced Security Posture
Curtain LogTrace strengthens your organization’s security by providing comprehensive records of file access, edits, and deletions. This detailed audit trail enhances visibility into data activity across your environment, supporting faster incident response and thorough incident investigations. With this level of transparency, organizations can more effectively identify patterns, trace the source of issues, and reinforce data protection strategies.
Streamlined Compliance
Meeting industry regulations becomes easier with Curtain LogTrace. It automatically captures file interaction logs that align with common compliance requirements, helping you maintain complete, tamper-resistant audit trails to satisfy auditors and regulatory bodies with minimal manual effort.

Increased Accountability
With clear, traceable records of user (file activities), Curtain LogTrace encourages responsible behavior and deters misuse. Organizations can assign clear ownership to file activities, ensuring that users are accountable for their interactions with sensitive or business-critical data.

Operational Efficiency
By simplifying file activity reviews and reducing the time needed for manual investigation, Curtain LogTrace improves internal processes. IT and compliance teams can quickly retrieve relevant logs and pinpoint events of interest — freeing up time for higher-value work.

Visibility & Transparency
Curtain LogTrace brings file operations out of the dark by creating a transparent environment where every critical change is logged. This clarity supports better decision-making, reduces risk, and fosters a culture of openness within the organization.
Use Cases
Compliance Auditing
Curtain LogTrace is essential for organizations that need to comply with regulations such as GDPR, HIPAA, or SOX. Its detailed logging and reporting capabilities ensure that every user action and system interaction is tracked, making it easier to pass audits and demonstrate compliance.

Insider Threat Detection
In scenarios where employees may attempt to access unauthorized data or perform actions that could harm the organization, Curtain LogTrace provides a detailed audit trail to prevent insider threats.

Incident Investigation
When security incidents occur, Curtain LogTrace enables security teams to quickly investigate the source, scope, and impact by analyzing detailed logs of all system and user activities.

Reference Industries
Finance and Banking
Protects sensitive transactions, ensures compliance (e.g., PCI DSS), and prevents unauthorized access with detailed logging and secure print watermarking.

Healthcare
Safeguards patient data and meets HIPAA requirements by tracking file and application activities and securing medical records.

Education
Monitors file usage and protects student records and intellectual property while ensuring data protection compliance.
Legal and Professional Services
Provides audit trails and secure file handling to protect client confidentiality and simplify compliance with legal standards.

Government
Ensures data protection, detects unauthorized actions, and supports regulatory compliance with centralized management and comprehensive logging.


Bundle with

Safeguard your screens with MonGuard’s advanced watermarking technology. Whether it’s protecting sensitive presentations or guarding against social engineering, MonGuard ensures your information stays visible only to those who need it.
Upgrade to comprehensive

Take your data security to the next level with Curtain e-Locker. This comprehensive solution integrates the best of File Activity and MonGuard, while adding critical features like Zone-Based DLP, Granular Access Control and other advanced features, giving you total control over your sensitive data.